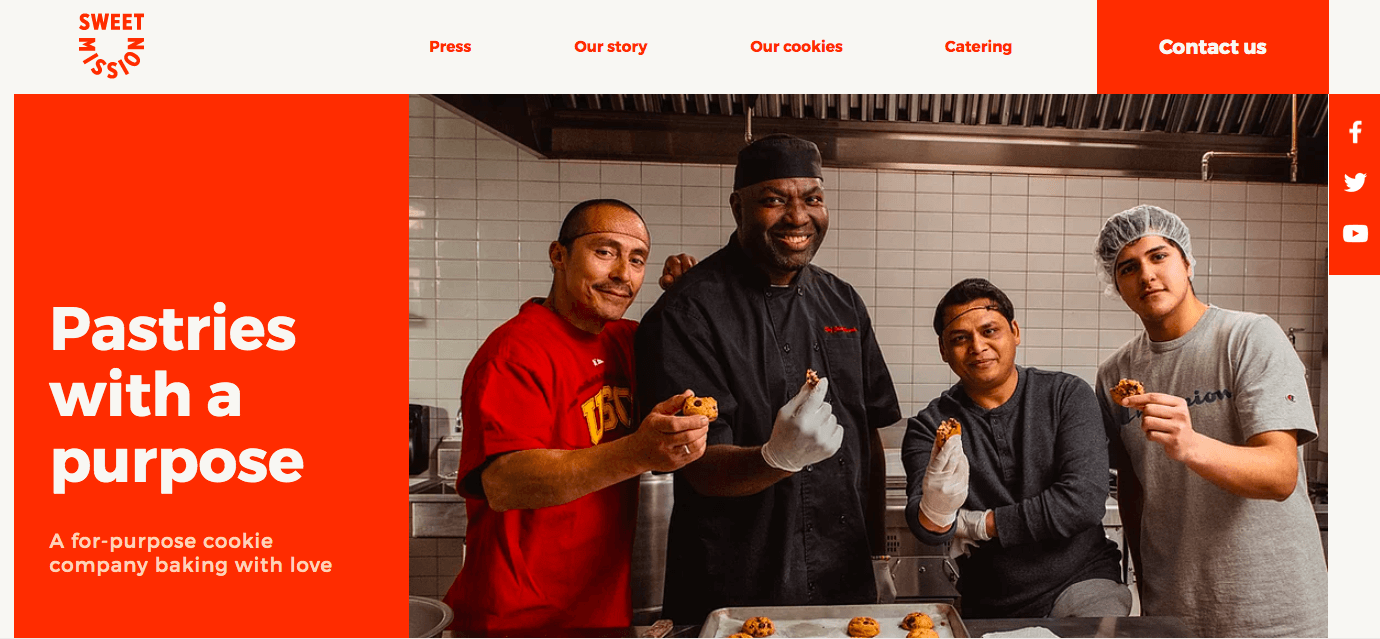
Anatomy of a Breach
Microsoft
This HTML native site analyses the various stages of a company security breach from the hacker’s POV. Highlighting the systemic weaknesses hackers look for most, the site presents Microsoft’s solutions to avoiding and overcoming such gaps in security.
Internet Marketing Association’s 2016 IMPACT – Best Infographic
View Work